Blockchain In Plain English

This is not yet another post, written by a tech geek, to another tech geek. The knowledge gap between the blockchain space and the community is getting wider day by day. The aim of this series is to explain how Blockchains work in the simplest manner, so that an average person can easily understand it.
There will be 4 posts:
Small recap: We have developed a basic PoW model for our protocol. Now let’s dive a bit deeper, and see if there will be any problem in the future.
In the previous protocol we developed, we were using round-robin fashion, and it was easy to predict who will create which page in advance. So, the attackers could easily DoS attack that person.
In PoW, however, we don’t know who will create the next page, since we don’t know who will be the first one to solve the hard problem.
We simply cannot know, because it the solution is found in a brute-force manner, hence it is resource+luck. So, who will the attacker perform the DoS attack on?
The whole network? Good luck with that Mr. Attacker :)
The whole network tries to solve the hard problem collectively. It really does not matter if someone disconnects from the network, or joins. Everybody is independent. Whoever solves the challenge, gets the right to create the new page.
We have mentioned, the lucky person who gets to solve the challenge, will broadcast the solution to the whole network. We also mentioned the network will be consisting of hundreds of thousands of people (at least, we want it to be). Isn’t this broadcast will become a burden and a bottleneck in our protocol?
Yes.
So will do a very nice trick, which is known for a long time, called Gossip Protocol.
This is just a 1-minute read with an illustration on Gossip Protocol
A very short summary for the lazy ones: you will not send your message to everyone, but only to your neighbours, and they will relay it to their neighbours, and so on… If you are curious about the details, THE LINK IS STILL UP THERE :)
Say that, you found the solution for the next block (congratz btw), and sent the block you just created to your neighbours. This newly created block includes the new transactions, the nonce you have found with your hard work (that allowed you to solve the challenge), the previous block’s hash, and the special transaction that adds money to your account as an award for your hard work. It’s up to you that who receives the new reward, it doesn’t have to be you. But many people are not that generous, so it is usually their own account.
What if someone decides to use your hard work (your Nonce), and changes the prize (the special transaction that adds new money to your account) by removing your special transaction, and adding one for his own wallet address.
Well, there are 2 solutions for preventing someone from stealing your solution in our case. One of them is easy, and only applicable to PoW; the other one is relatively complicated, but a general-purpose one. Here is the general-purpose solution: (you do not need to read this to understand Blockchain, read it only if you are curious about Cryptography).
Here is the easy solution: we just do nothing and allow it, because we do not need to prevent it. HAHAHA!
We allow it, because this attack simply won’t work. Remember, the solution for the challenge is, finding such a Nonce, that the WHOLE content
of the block will be hashed, and the first 10 digits of that hash will be 0s. The WHOLE content includes, your account too.
If the stealer tries to change the special transaction by replacing his wallet address with yours, then he would need to compute a
new Nonce from scratch. In other words, he has to solve the challenge in an honest way in this case, has to spend his own effort.
What if the attacker does not change anything from the block, but claims that “this is MY block, and I’m generous, so I’m giving the reward to this random account”. In theory, he can do that. In practice, he can’t.
We don’t have any protection against this (somebody else claiming the ownership). Anybody can claim that the solution is theirs. That’s why in theory, it is possible.
In practice, all these things are automated (receiving new transactions, gossiping, trying to solve the puzzle for the next block, etc.). So you are not actively listening for incoming messages, and selecting options to reject/accept them. The software you are running on your computer handles them as a background process. The message “This is MY block, I’m generous, blah blah…” will be received by the background process, and won’t be read by any humans, and effectively will be ignored. In short, we don’t care about who found which block. We don’t care about extra messages. We only care about the transactions in the block (and whether the block is valid).
We made it! We don’t need anything else. Our protocol will now run just fine! Of course, there can be optimizations, but let’s not bother with them (I wanted to write a post, not a book).
Understanding forks, will let us have a very solid understanding of PoW. Smart-Ozgun previously said (in the previous post), “if we tune the hardness accordingly, it will be nearly impossible for 2 people to find a solution simultaneously”. He is right. However, it is nearly impossible, not completely. And as you guessed, yes, it happens from time to time.
So, what happens when there are 2 valid candidates for the next block? Remember, although they are solutions to the same challenge, they are different blocks, they are found by different people, and their special transaction is different, hence their nonce is different. Yes, it is possible. Which one should we accept? There is no right answer to this question. We will just go with one, and ignore the other. Which one? Doesn’t matter.
Bad news, probably there will be some people accepting one of the solutions, and some other people that will accept the other one. Now, the network has been divided into two. We call this a fork. Look at the (a) part of the image.
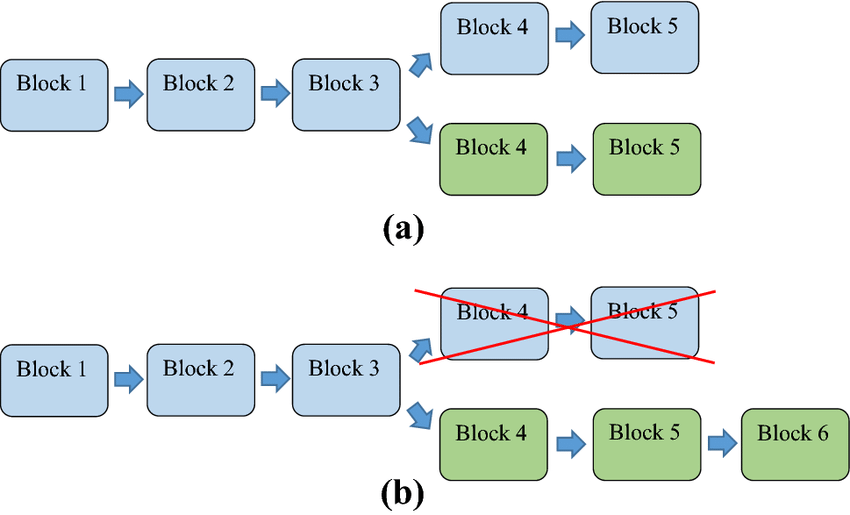
The challenges were based on the previous block’s hash. So, yes, there are 2 simultaneous challenges going on at the moment. Both of the forks are valid. The good news is, there is a way out of this situation. At some point, one of the forks will become longer (b). And PoW states that, we can always trust the longer chain. The longer chain will always be honest. This doesn’t necessarily mean that all the shorter forks are dishonest. But it is for sure that the longest one is honest. Hence, we have a pretty solid reason to select the longer chain.
I like this analogy a lot:
Imagine we are to dig a tunnel through a big mountain. Digging a tunnel is hard work. And also, if we have more machines, the
tunnel will progress faster (the more computing power you have, the more possibilities you can try for brute-forcing, and faster
you can find the Nonce, and add 1 more block to the chain, making it longer). It is a perfect analogy!
What does a tunnel represent in this analogy? The blockchain itself, the record of the transactions.
What do machines represent in this analogy? The computing power, CPU, GPU, ASIC, etc.
Recall our assumption in every blockchain, at least 51% is honest.
Now, imagine we have 100 equal machines in total (representing the whole computation power of the network), to dig a tunnel. Assume the worst, only 51 of these machines are digging the honest tunnel. This is the honest tunnel, since people decided they will dig only one tunnel (who wants alternative histories of transaction records, there should be only one :D)
Some minorities can start forking the honest chain (forking the tunnel), or start from scratch (digging a completely new tunnel) with their machines. We cannot prevent that.
But, this minority can have at most 49 of these machines.
Now, which tunnel will be longer, the one that is being dug by at least 51 machines, or at most 49? As long as we have 51% honest, the longest tunnel will always be the honest tunnel. That is the beauty of PoW, and it is this very property that rendered many of the other consensus algorithms legacies (51% honesty is enough for the system to work).
Now, in the first article, Pete was in a rough spot to select which version to trust (Sal and Brian had cheated). Pete could solve that, by trusting the majority. But he had to ask every single person in the network to do that. This is a very bad solution considering that blockchain is meant to be a worldwide protocol.
Instead of asking everyone, we can simply accept the longest chain in PoW. If someone provides a chain that is longer than what we currently have, without any questions, we accept it. Why? Because 51 machines will always dig the longest tunnel.
This is the last question that we need to understand, to be able to say that “Yes, I know how PoW works at a high-level”.
“This was only high-level?” you might ask. Yes, it was :)
If you want to dive deep, I suggest Mastering Bitcoin, available as an online and free resource, just google it.
Coming back to the question, we should make an important distinction.
The blockchain itself is mutable (we are constantly adding new transactions to it). The data we already stored, is immutable. We cannot change the history.
Why?
Imagine we solved the challenge for the next slot, and made the chain longer. So, people should accept our version of the blockchain, since ours is longer. Knowing that, we also made a change to a previous block (removed a transaction as Joe and Brian did in the previous article).
Again, we can do this. Nothing or nobody is preventing us from doing that. But people won’t accept our version of the chain now. Because they can detect what we have done easily. Let’s demonstrate what will happen with a small example:
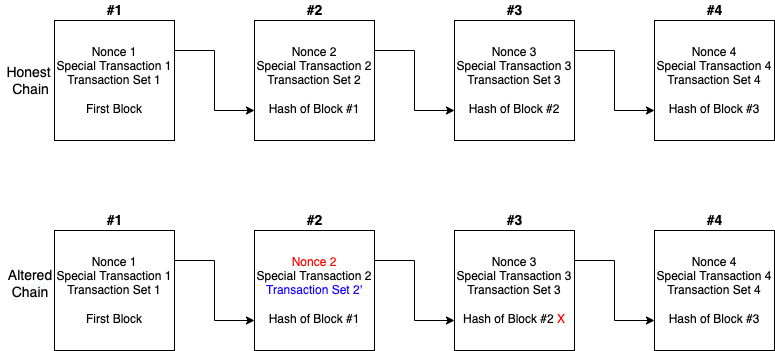
Say that we wanted to remove a transaction from the Transaction Set 2, and made it Transaction Set 2'. Now, there are 2 problems.
Nonce 2 is no longer producing a correct solution for Block #2. This means, somebody was naughty.Hash of Block#2 stored in Block #3 is not matching the value when we compute the hash of the altered Block #2. This also indicates
somebody was naughty.So, we can be sure that, there won’t be any modification in the honest chain. Else, it won’t be accepted by other people.
This is the most dangerous scenario for PoW. Imagine someone was able to generate two valid candidates (say A and B) for the next block. And also, imagine
that he is buying a Ferrari with his money in the candidate A, and buying a Lambo with the same money in the candidate B. He doesn’t have enough money for
both Ferrari and Lambo, he can afford only one of them. Basically, he is trying to double-spend.
Since both A and B are valid on their own, he can publish A to half of the network, and B to the other half of the network.
In PoW, we don’t actually have any way to prevent that. But the longest chain will help us. Remember what would happen when there is an honest fork
(both chains are valid). Eventually, one of the chains would grow faster than the other one. I won’t dive into mathematics of that, but some genius people
calculated that, it is practically impossible for both chains to grow at the same rate for 6 blocks.
And when one of the chains becomes longer than the other, that chain becomes the valid chain, invalidating the shorter one. What we could do for this
double-spending issue is, we can wait for 6 blocks to confirm transactions. So the seller of the Ferrari and Lambo should wait for 6 more blocks,
before actually handing the car over. In this case, say the chain with block A got longer. Lambo seller would see that the longest chain does not have any
transactions for the purchase of this Lambo. So he would cancel the deal.
51% attack assumes that, the attacker has the 51% of the computing power of the whole network.
Say that, we are on the 10th block, and the next block will be the 11th. The attacker would spend his money in an honest way, and buy a Ferrari (this transaction will
be in the 11th block). Waits for 6 blocks (say we are at the 17th block right now), and happily gets his car. Then, the attacker forks from the
10th block (or, ignores all the blocks that came after the 10th block), and starts to mine an alternate chain from the 10th block. The attacker won’t include
the transaction that he bought the Ferrari in this alternate chain. Since the attacker has 51% of the computing power, this new alternate chain that our
attacker mines, will eventually become the longest chain. Since he did not spend his money on this fake alternative chain, he can basically double-spend his
money again.
What can we do against this?
Nothing.
Should we be worried? No. If 51% of the power is compromised, if 51% of the users are corrupted, it is already game over.
Imagine 51% of the people went crazy. If crazy ones are the majority, the society is done for. You are living your very own lives on the assumption that the majority will be not corrupted. PoW is not different.
Previously, when I tried to explain what is PoW to a crypto-outsider, I was telling them, PoW is for preventing double-spending, PoW is like a global clock. And of course, they were having difficulty understanding it. They always asked the question “but why do we need a hard problem?”.
This indicated that, I’m the faulty one here. I was not explaining it right.
As we saw in the 2nd post of this series, we don’t actually need PoW to prevent double-spending, nor for a global clock. Taking turns for selecting the leader (round-robin fashion) solves both of these problems. But this naive approach created two other problems:
PoW is also preventing double-spending, without compromising decentralization.
I have just the metaphor for this confusion! It’s not 100% accurate of course, but will be enough to make my point :)
If we tell someone “we need rollerblades, because they are protecting our feet from wind, and keep them warm”, they will not understand what we are trying to say, right? Rollerblades are sledgehammers to crack a nut in this case. A simple shoe can keep our feet warm.

Imagine an utopia that DoS attacks are not possible. And imagine we want to build this blockchain among our friends, so we know each ones identity, and we know for sure that they will not quit the system. Why bother with PoW? Round-robin is fine for this situation.
Recall from the Two Birds With One Stone: Basically, we will randomize the selection of the block creator. Why? Because we don’t want DoS attacks in our protocol. We also want everybody to be able to join or leave the protocol whenever they want. Basically, we want decentralization.
This is what PoW is doing. The aim of PoW is:
Randomize the selection of the block creator, in a secure, and fully decentralized way. Its main goal is not to prevent double-spending, not to act as an internal clock, not to establish consensus (ordering) on transactions, not other things. These could be achieved via much simpler mechanisms. I’m not saying that PoW is not doing them. These are also achieved by PoW, but as side effects, or as benefits that indirectly come because of the main one: randomizing the block creator.

If we select a block creator, then we automatically achieve consensus on the ordering (also prevent double-spending).
The work we have to do in Proof of Work consumes time, then yes, each turn can represent the tick of a clock.
This is, I believe, the most important thing you could learn from this article. PoW is a randomizer for the block creator (whilst preserving decentralization and security).
PoW is revolutionary, and ingenious!
But like everything else, it also has some drawbacks. You probably heard that Bitcoin (which uses PoW) is consuming electricity as much as a small nation. This is not good for sure, nobody is endorsing electricity usage. This is seen as a cost of having a secure and decentralized distributed ledger. The good news is, with the new promising technologies, we can still achieve the same amount of decentralization and security, with much much much less electricity usage. The two biggest candidates for that are Proof of Storage, and Proof of Stake, and many more variations. Feel free to dig the internet for more!